Required Annual Cybersecurity Awareness Training
WCU prioritizes annual cybersecurity awareness training to help you recognize and respond to potential threats. This year’s training will launch at the beginning of February. Please watch for details in your inbox.
Employees in need of a computer or a space to complete the module should contact the Faculty & Staff Training office (fast@wcupa.edu) for accommodations.
Stay Cybersafe
It is important to remember to Be Cyber Smart and Think Before You Click. Bad actors are intensifying their efforts to trick unsuspecting users into scams that can steal your credentials, inject malware onto devices, or obtain credit card information by falsely selling products. Common phishing message types include impersonation messages (posing as a professor, colleague or friend), fake job offer scams and false “Shared Document” notifications. Bad actors have even begun to utilize QR codes in emails to circumvent common email security filters and trick targets into visiting malicious websites. Higher education institutions are often targeted especially when users are focused on exams and projects and less likely to spot a scam.
Things to consider to navigate safely and securely:
-
-
-
- Think before you click. If an email looks suspicious or an offer looks too good to be true, it probably is.
- Don’t fall for fake delivery notifications or text messages.
-
-
Security University
IS&T encourages everyone to take increased ownership of enhanced online activity and the important security practices that come along with it. The virtual safety of our community, and, ultimately, our nation, depends on our personal online safety practices. Cybersecurity is important to West Chester University and we are committed to helping our faculty, staff and students become more resilient.
Stay Protected While Connected
Before you connect to any open/public wireless network (like at an airport, hotel, or cafe) be sure to confirm the name of the network and exact login procedures to ensure that the network is legitimate. If you use an unsecured public access point, practice good internet hygiene by avoiding sensitive activities (banking and shopping) that require passwords or credit cards. Using a personal hotspot or cellular data is often a safer alternative to free Wi-Fi. Only use sites that begin with "https://" when online shopping or banking.West Chester University's RamNet WiFi is a secured network. It is secured by an enterprise network authentication protocol called 802.1X. Using this protocol, all network traffic, including usernames and passwords, are encrypted during transmission. During the connection process, usernames and passwords are checked to verify that the user is an active member of the WCU community. Once confirmed, appropriate network access is assigned based off network needs and requirements. Remember, free Wifi could cost you .
Fight the Phish
Play hard to get with strangers.
Cyber criminals use phishing tactics hoping to fool their victims. If you are unsure who an email is from (even if the details appear accurate) or if the email looks "phishy" do not respond and do not click on any links or attachments found in that email. For help determining if an email is legitimate, forward it to HelpDesk@wcupa.edu.
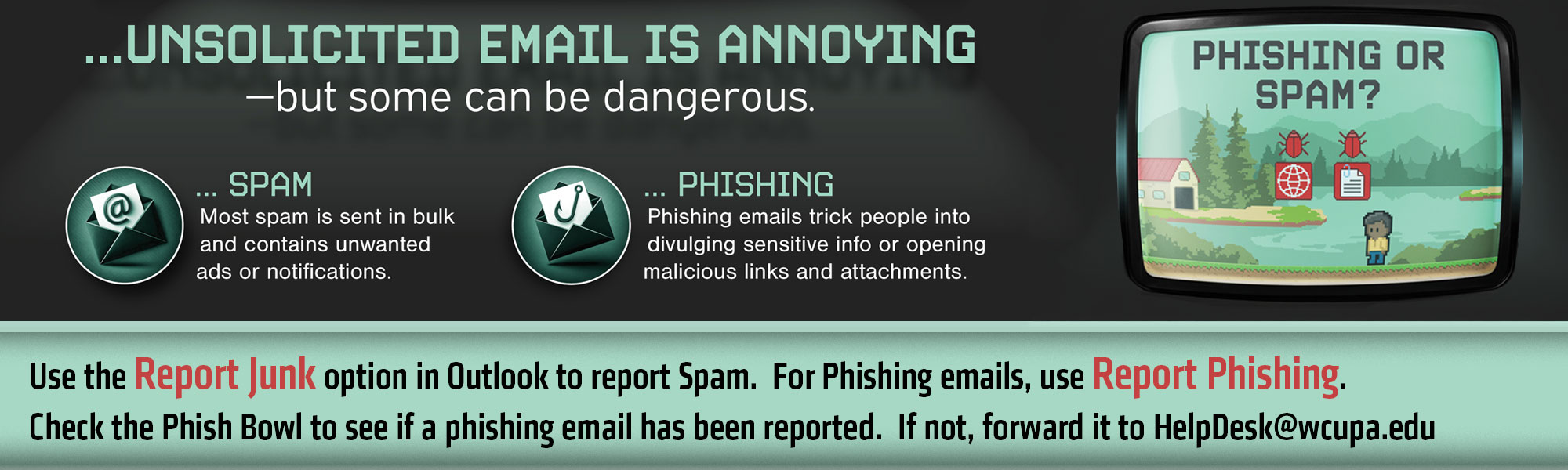
Understanding Spam vs. Phishing
Not all unwanted email is dangerous. Spam is typically bulk advertising or promotional messages that are annoying but not harmful. Phishing, on the other hand, is designed to trick you into revealing sensitive information or clicking malicious links or attachments. If you receive spam, use the Report Junk option in Outlook. If you believe a message is phishing, use Report Phishing instead. Reporting helps the email system to better filter unwanted email and block malicious email in the future.
Check the Phish Bowl.
For a list of recent email messages that have been confirmed as malicious or fraudulent by Information Security. If you believe you've recieved a phishing email, check the Phish Bowl to see if it has already been reported. If it’s not listed, please forward the email to HelpDesk@wcupa.edu so Information Security can review it.
Deny a Duo login approval request if you did not initiate it.
Imagine you are getting coffee with friends and you receive a Duo Multifactor authentication request on your phone. You suspect that it is fraudulent because you are not trying to log into any systems or accounts. What should you do? You should deny the request.
Social Media Cybersecurity Tips
Never Click and Tell.
Limit what information you post on social media. Popular quizzes often ask users a series of shareable personal questions, ranging from the name of their pet, childhood best friend, first grade teacher or their birth city. Some people see them as a fun way to bond with friends, but many of these queries are similar if not identical to security questions used when setting up accounts at banks and other organizations. Keep Social Security numbers, account numbers, and passwords private as well as specific information about yourself such as your full name, address, birthday, etc.
Think Cybersecurity First
Cybersecurity is a year-round effort and staying safe online is increasingly important as our world continues to operate virtually for so much of work and play. We should all approach cybersecurity with care in owning, securing, and protecting all our online accounts, data and information. West Chester University offers these resources that you can utilize to keep yourself safe online:
- CISA’s Cyber Essentials – basic cyber best practices for business leaders: cisa.gov/cyber-essentials
- Learn about careers in cyber with the National Initiative for Cybersecurity Careers and Studies: niccs.cisa.gov
*National Cyber Security Alliance (NCSA) and the Cybersecurity and Infrastructure Agency (CISA) content is copyrighted and reproduced under the Creative Commons BY-NC-ND 3.0 or Creative Commons BY-NC-ND 4.0 license.
Information Security Tools @WCU
WCU has various methods of offering Information Security and Privacy programs. Information Security can only be achieved with lots of layers (like an onion.) One of those layers is the concept we sometimes call the "Human Firewall." Many times this is the first layer that protects the confidentiality, integrity and availability of data and IT services. This means YOU. However, in order to make that achievable, WCU has provided a few services and educational opportunities to assist you.
DUO Multi-Factor Authentication
DUO Multi-Factor Authentication protects your digital identity from being compromised
even if your password is exposed to bad actors.
Proofpoint Email Security Gateway
Proofpoint is a leading platform for protecting against phishing, malware, and spoofing attacks that come through email. Proofpoint provides protection against the threat of data breaches at the University.
Cybereason
Cybereason is an Endpoint Detection and Response (EDR) system that detects suspicious activity, uncovering attackers’ behavior patterns and empowering IS&T to detect and stop emerging attacks. As part of a multi-pronged approach to enhance endpoint security monitoring, all university owned laptops and desktops now require an application called Cybereason.
Phishing Simulations
Phishing simulations help users learn to recognize, avoid, and report potential threats that can compromise accounts, critical business data and systems. Just one compromised account can put valuable computing resources and sensitive institutional or personal data at risk of exposure. Even accounts with limited or no access to confidential material can be weaponized to attack and compromise additional user’s accounts until one with sufficient privileges is targeted and taken over. Every account matters.
PhishBowl
If you receive a suspicious email, you can visit The Phish Bowl to view a list of latest phishing attempts. If the email is posted, then the email has already been reported, and you can simply delete the email. How to Spot and report a Phish or Spam email.
Phishing Red Flags:
For your safety and security, please consider the following red flags if you receive
a job via email that is not coming from Handshake, or from a professor, student, or
staff member at the university that you know and trust.
- Is a personal assistant job, or a job where the employer is not named
- Comes from an email address that doesn’t match the company’s name
- Does not provide information, such as the title of the person sending the email, the employer’s address or phone number, etc.
- Offers to pay a large amount of money for not much work
- Offers you the job without interviewing you
- Asks you to pay an application fee or some other fee as a condition of starting employment
- Wants you to transfer money from one account to another, by wire service, courier or other means, or deposit a check that they send you
- Requests your bank account or credit card information
Remember:
No legitimate employer will send payment in advance and ask you to send a portion
of it back to them. These jobs are often posted as a personal assistant or administrative
assistant and ask for assistance in depositing checks or doing mystery shopping. These
checks are fraudulent and can end up costing you hundreds of dollars.